SSO.OIDC with Okta
This guide will show you have to set up a Okta SSO.OIDC connection for TigerGraph.
1) Create an Okta Account
-
Create an OIDC application on Okta, here is a guide from step 1 to 10 How To Set Up Your Own Okta App (OpenID Connect)
-
Register an account and login Okta.
-
Below are some main detail information for settings and then select save.
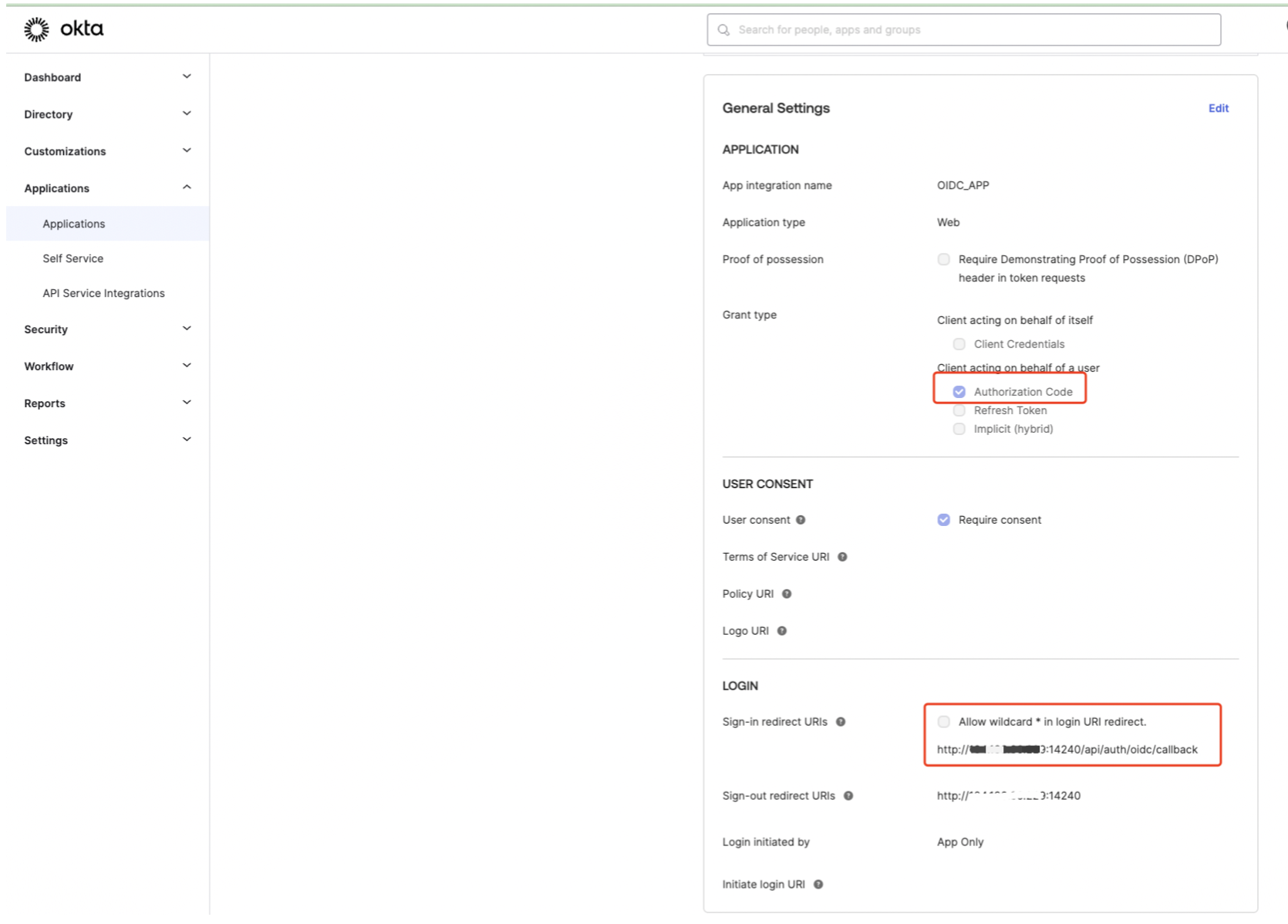
-
For the Sign-in and Sign-out redirect URIs the IP(s) can be replaced with your own IP instances.
For example:
2) Configure TigerGraph Backend
-
Set configurations on the TigerGraph backend.
-
Check the
GUI.Cookie.SameSiteconfig (default is3)Example:GUI.Cookie.SameSite Default mode: 1; Lax mode: 2; Strict mode: 3; None mode: 4
-
If the SSL instance is enabled, set
GUI.Cookie.SameSiteto4. -
If the SSL instance is disabled SSL, set
GUI.Cookie.SameSiteto3. -
Set via the command:
Example:gadmin config set GUI.Cookie.SameSite 3
-
-
Get Okta configuration using this URL but update
your_okta_app_domainwith your Okta domain:https://your_okta_app_domain/.well-known/openid-configuration
Example:https://dev-710975.okta.com/.well-known/openid-configuration
-
Login to TigerGraph backend and set the OIDC config entry via the command, you will need two items from your Okta account:
-
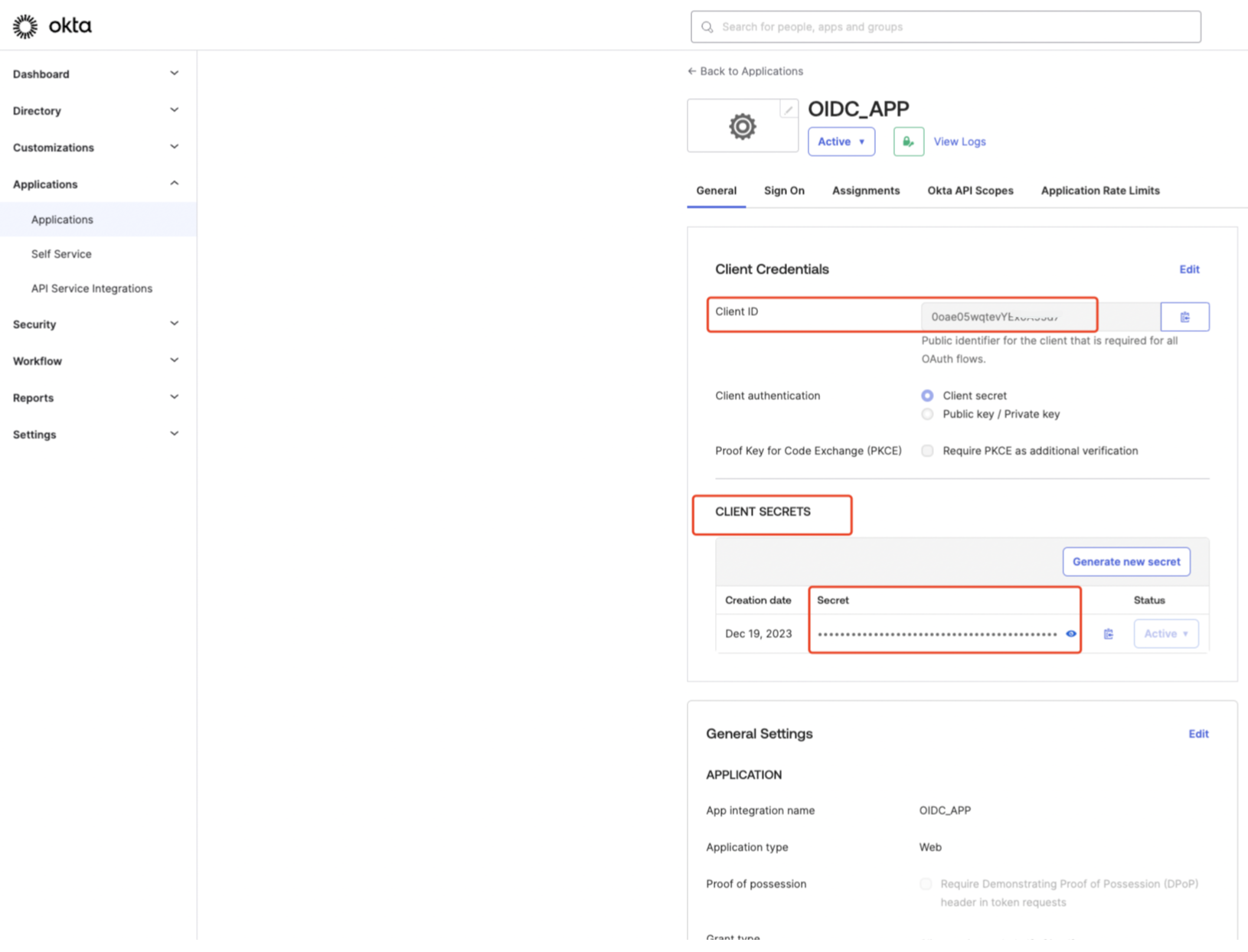
Security.SSO.OIDC.OP.ClientId : This is your application
clientIdon Okta, after your created an OIDC app on Okta, you can find it in configuration. -
Security.SSO.OIDC.OP.ClientSecret : This is your application
clientSecreton Okta, after your created an OIDC app on Okta, you can find it in configuration.
-
-
Start the configuration process with this command
gadmin config entry OIDC
Below is a configuration example:tigergraph@oidc-centos7-0:/home/graphsql$ gadmin config entry OIDC Security.SSO.OIDC.Enable [ true ]: Enable OIDC based SSO [true/false]: default false New: true Security.SSO.OIDC.CallBackUrl [ http://your_tigergraph_instances_IP:14240 ]: TigerGraph service provider callback URL: default http://127.0.0.1:14240 New: http://your_tigergraph_instances_IP:14240 Security.SSO.OIDC.ResponseType [ code ]: Define the kind of credential that OIDC provider will return [code/token/id_token/code id_token/...]: default code New: code Security.SSO.OIDC.Scope [ openid profile ]: Specifies the claims (or user attributes) to retrieve, separated by a space [openid email/openid profile/...]: default openid profile (means user's full profile). New: openid profile email Security.SSO.OIDC.BuiltinUser [ __GSQL__oidc ]: The builtin user for OIDC, default: __GSQL__oidc New: __GSQL__oidc Security.SSO.OIDC.ClaimAsUserID [ email ]: The OIDC claim which will be used as username in TigerGraph, default: email. New: email Security.SSO.OIDC.OrganizationId [ ]: The organization ID for cloud OpenId server, internal use only for TG cloud. New: Security.SSO.OIDC.OP.SSOUrl [ https://login.okta.com/oauth2/v1/authorize ]: Single Sign-On URL: default https://op.example.com/oauth/authorize New: https://login.okta.com/oauth2/v1/authorize Security.SSO.OIDC.OP.Issuer [ https://login.okta.com ]: Entity that issues a set of claims, example: https://example.issuer.tigergraph.com. New: https://login.okta.com Security.SSO.OIDC.OP.AccessTokenURL [ https://your_okta_app_domain/oauth2/v1/token ]: The API to request access token from OP, not needed for OIDC implicit flow, example: https://op.example.com/oauth/token. New: https://your_okta_app_domain/oauth2/v1/token Security.SSO.OIDC.OP.UserInfoURL [ https://your_okta_app_domain/oauth2/v1/userinfo ]: The API to request user information via access token, not needed for OIDC implicit flow, example: https://op.example.com/userinfo. New: https://your_okta_app_domain/oauth2/v1/userinfo Security.SSO.OIDC.OP.ClientId [ 0oae05wqtevYEx0A55d7 ]: The client id assigned by Openid Provider when registers TigerGraph New: 0oae05wqtevYExxxxxxxxxx Security.SSO.OIDC.OP.SigAlgorithm [ RS256 ]: Define the algorithm that OIDC provider used to sign the ID token, [RS256/HS256/...]: default RS256 New: RS256 Security.SSO.OIDC.OP.ClientSecret [ BUxbeyK0eVpboa7Vdv5kJafgNi4beux1UNUhLPvjbdX1emae8gwtN8oHp3eoKcey ]: The client secret generated by OIDC provider, this config is only needed if algorithm is HMAC type New: BUxbeyK0eVpboa7Vdv5kJafgNi4beux1UNUhLPvjbdX1emae8gwtN8oHxxxxxx Security.SSO.OIDC.OP.JWKSUrl [ https://login.okta.com/oauth2/v1/keys ]: The url of the OpenID provider to retrieve the public JSON web key set, e.g. https://op.example.com/.well-known/jwks.json. It is only needed if algorithm is RSA type New: https://login.okta.com/oauth2/v1/keys [ Info] Configuration has been changed. Please use 'gadmin config apply' to persist the changes. tigergraph@oidc-centos7-0:/home/graphsql$ gadmin config apply -y
-
-
3) Setup OIDC Button
After above operations, you will see the login via OIDC button on TigerGraph.
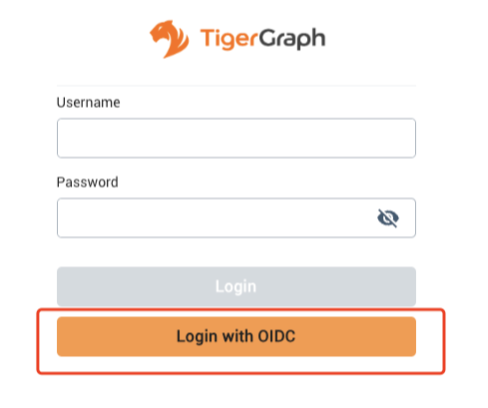
-
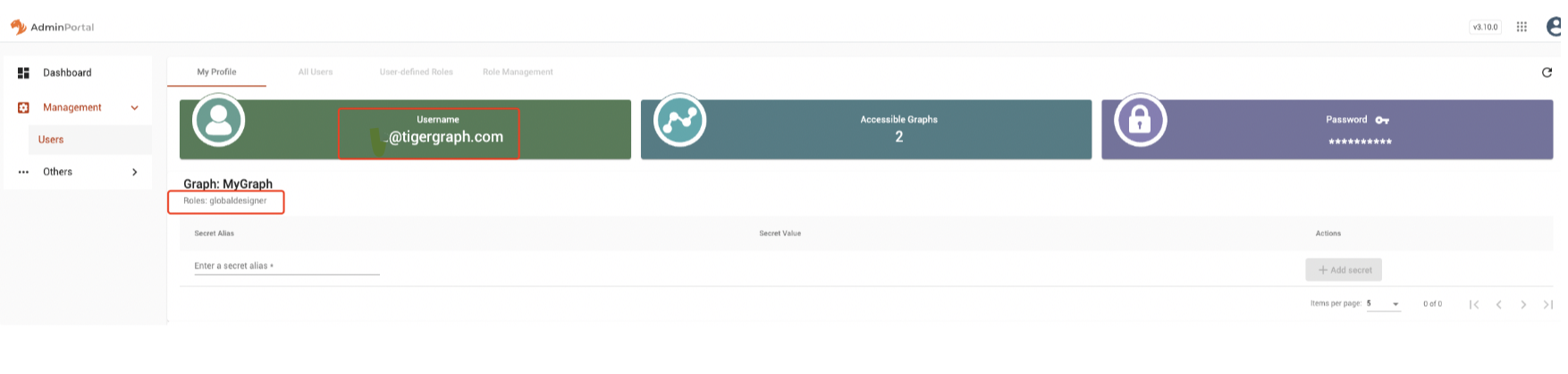
Now, grant a role to a OIDC user on TigerGraph via Admin Portal
-
Login to TigerGraph via
superuser(tigergraph) -
Go to
-
Click tab:
-
Click Add Group
-
Type the group name, attribute name and value, name depend on
Security.SSO.OIDC.Scope.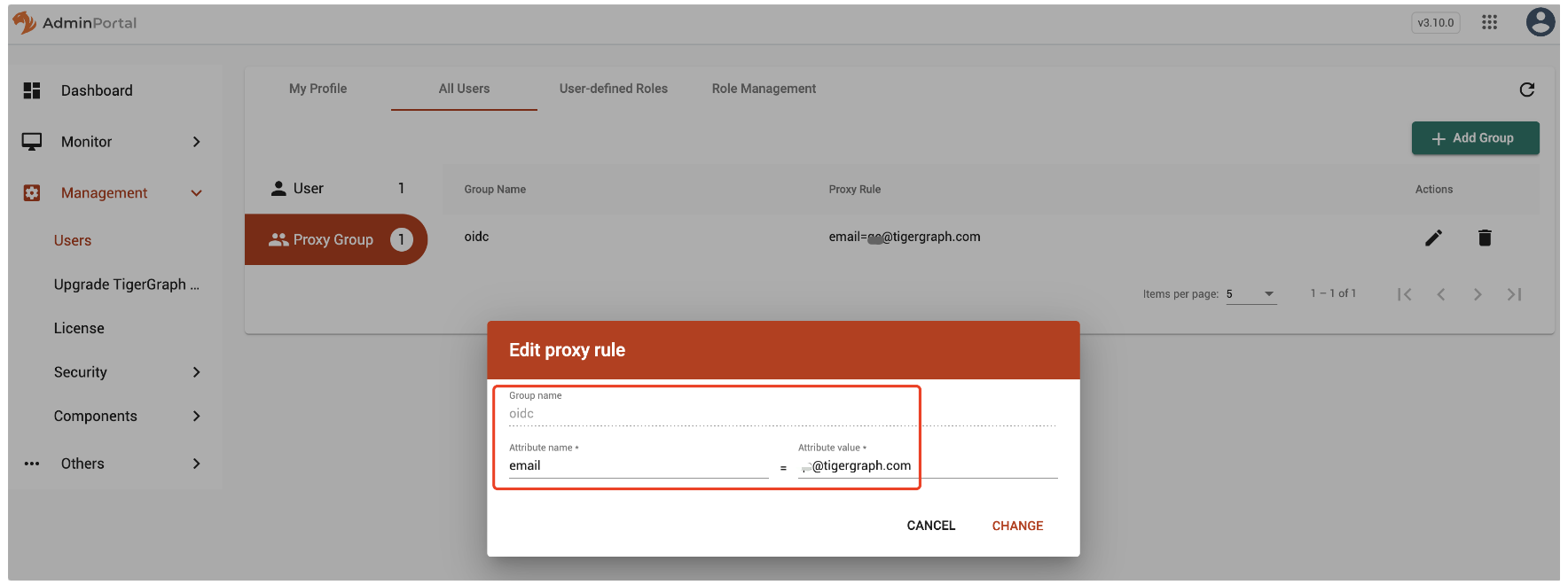 Figure 1. Type the group name, attribute name and value
Figure 1. Type the group name, attribute name and value
-
-
Now, grant a role for the
Proxy Groupand save.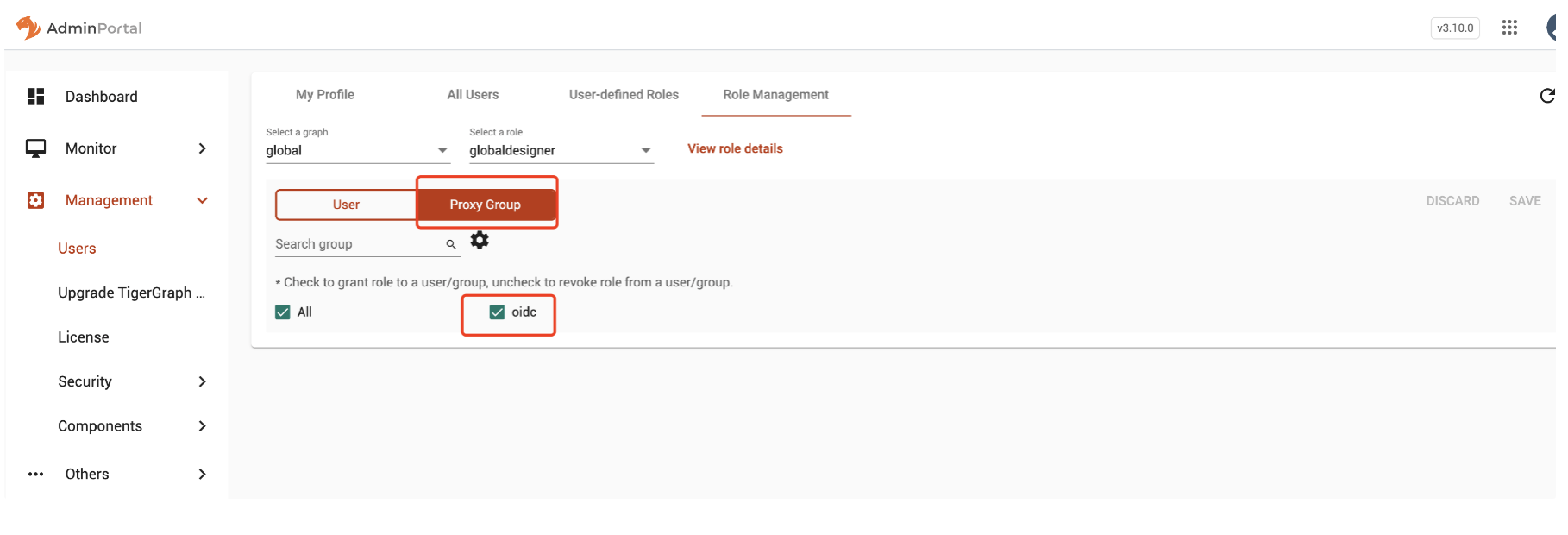 Figure 2. Example
Figure 2. Example
-